Firewall Administration
The new InJoy firewall™ delivers an accomplished range of capabilities that quite simply blows away the competition, at a fraction of the cost.- Easy GUI Administration
The fully customizable Firewall desktop management GUI delivers color-coded security alerts, intuitive configuration wizards, real-time traffic visualization, AES encrypted platform-interoperable remote management, and a wealth of pre-configured log file monitors. - Superior Protection
In just a few minutes, your network could be protected by a solid combination of both traditional and next generation firewall technologies. It's broad-scoped security that holistically protects the business and with 10+ pre-configured security templates you don't need to be a security expert to get started. - Access Management
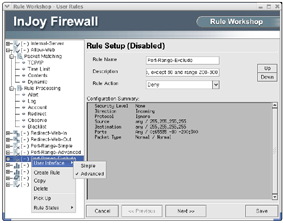
Use the Rule Workshop configuration wizard to easily create access control rules, traffic shaping rules, redirection rules, time-based rules, IPSec specific rules, whitelist rules, dynamic/static blacklist rules, pre- or post processing rules, alert rules, flexible log rules and traffic accounting rules. - Traffic Shaping
It takes just a single high-speed session to monopolize even the fastest connection. With traffic shaping you can ensure Quality of Service (QoS), prioritize interactive traffic, limit bandwidth for any type of traffic and even divide bandwidth between users in a group. - IPSec VPN Support
Set up a Virtual Private Network (VPN) with the seamlessly integrated multi-platform IPSec support. Use the intuitive VPN Wizard to easily configure a company-wide VPN or use the Tunnel Workshop to have full control of the individual security associations (for full flexibility and the best possible third party interoperability). All the latest features supported, including NAT Traversal, X-Authentication (including external storage driven authentication), RSA Signatures, x.509 Digital Certificates, high-speed AES encryption, and Blowfish. Ideal for serving as the corporate VPN Gateway or as secure VPN Client out in the field. - Gateway Capability
With no reconfiguration of network applications, the Network Address Translation (NAT) feature provides optimized and transparent Internet access for all computers on your private network. Rapid, trouble-free and measurable deployment is ensured through convenience features, such as DNS Forwarding, the built-in DHCP Server and NAT client statistics. - Multiple Access Technologies
The InJoy Firewall™ supports Ethernet connections of any type, including PPPoE, PPTP, satellite connections, DHCP served connections, wireless, or plain lan-to-lan. PPPoE users enjoy automated link monitoring, demand connections, and scripting in order to maximize the use of dynamic IP addresses.
Technology Benefits
The InJoy Firewall™ utilizes optional feature plugins and the latest Firewall technology to set new standards for security, usability and management.- Modular
Buy and learn how to use a single product, which then easily morphs and scales to solve your specific requirements. Plug in new features without introducing new problems and without having to worry about capacity problems, new offices, or changing network topologies. Disable unused code to minimize the code path, increase performance and prevent potential problems in "dead" code. - Self-contained
For a truly portable, mission-critical and standards-based solution, all major features — including IPSec, PPPoE, PPTP and firewall security — are implemented from the ground up using InJoy's own hardened codebase. It's comparable to hardware solutions — just less expensive, easier to install, and with all the benefits of software. - Deployment Friendly
To enable rapid enterprise deployment and ease of use, the InJoy Firewall™ supports both GUI and text file configuration. The Firewall Server process can be run invisibly in the background, directly on your desktop, or as a Windows Service. 1-minute installation - Graphical or Script Based - ensures trouble-free deployment, and swift recovery after OS re-installation.
Firewall Administration
Firewall security is too important to be confusing. Busy professionals require low-admin technology to successfully measure, visualize and manage their networks.Efficiently manage one or more InJoy Firewall™ Servers from your desktop — locally or remotely. With platform interoperable GUI connections, you only need to learn a single tool, saving you time and costs.
Executive Overview
At the heart of InJoy Firewall™ is the comprehensive and easy-to-use InJoy Firewall™ GUI, which enables you to:- Visualize
Detect anomalies and monitor bandwidth statistics. Gain real-time insight into Firewall status and network utilization. - Measure
Investigate alerts and rejected traffic, monitor employees' HTTP requests, blacklisted users. IPSec tunnels, policy violations and much more... - Configure
Customize security levels, create access rules, shape traffic, blacklist users, define IPSec tunnels and maintain IPSec user accounts. - Manage
Enjoy the flexible set of commands and the ability to manage multiple InJoy Firewall™ Servers across platforms. Multiple instances of the GUI can run simultaneously; each of these can connect securely to Firewall Servers either locally or remotely, greatly simplifying administration tasks.
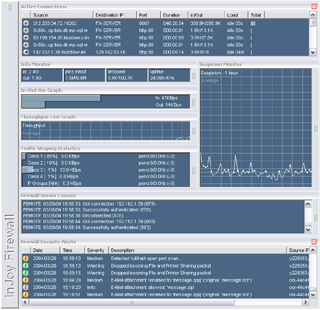
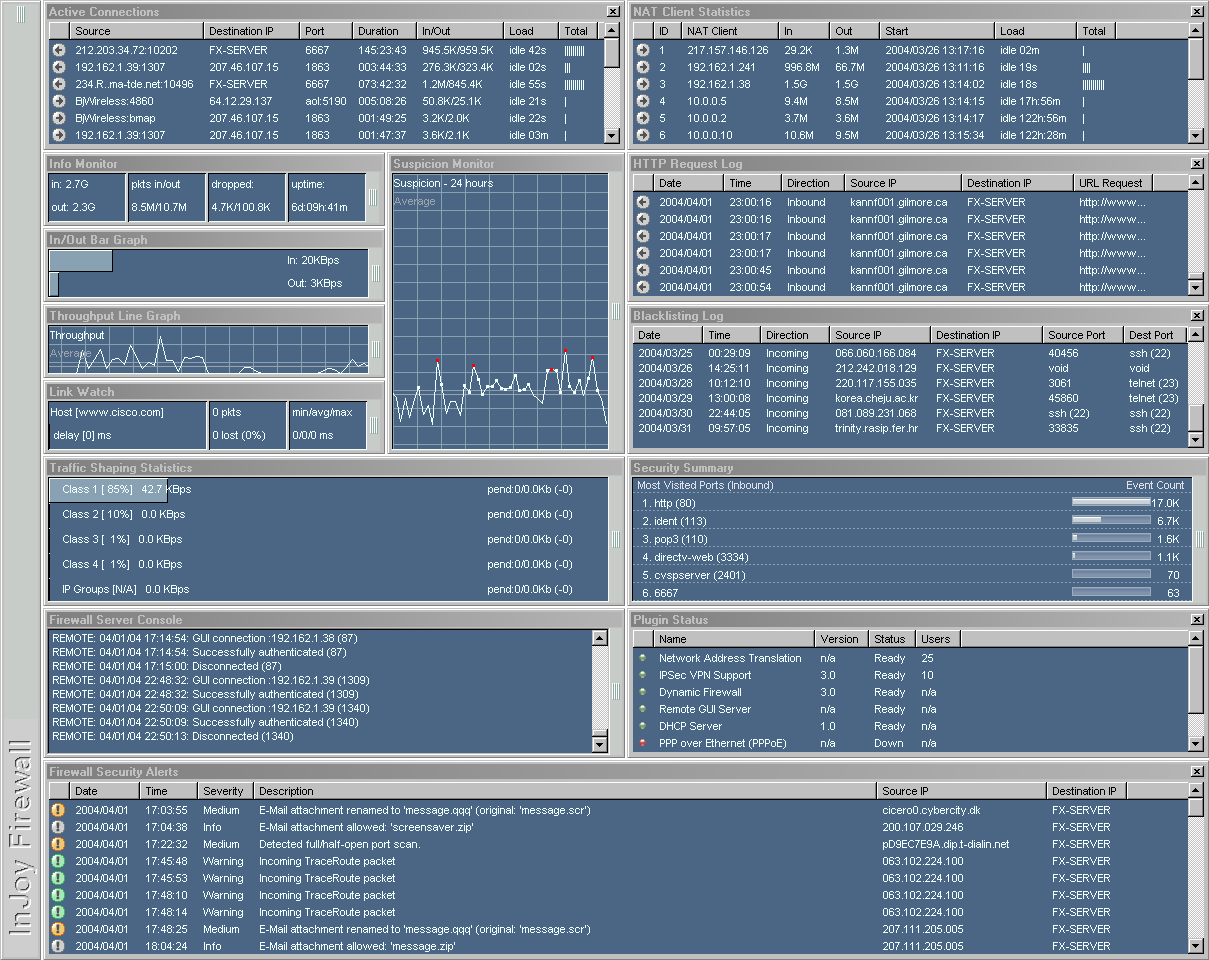
Visualize
The visual appearance of the Firewall GUI is highly configurable, allowing network administrators to tailor the appearance to suit their own — or the customer's — unique computing environment and needs.- Visual Schemes allow you to view just the information that is important to you, thus increasing your ability to quickly detect suspicious behaviour and and minimize the impact on your desktop experience.
- Font and Color Palettes allow you to create visual cues to distinguish GUI instances when you manage multiple firewall servers
- Graphical Bandwidth Monitors show the amount of data being scanned per second, giving you an instantaneous visual representation of your network's inbound and outbound traffic.
- The Information Monitor provides accumulated data-transfer statistics, dropped-packet statistics, and firewall server uptime statistics.
- The Active Connection Monitor provides real-time visualization of firewalled connections, including their duration, idle time, data-transfer statistics, IP numbers and port numbers.
- The Link Watch Monitor shows the link quality by means of graphical Ping statistics. The Monitor can be configured to give an audible alert if the link disappears.
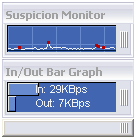
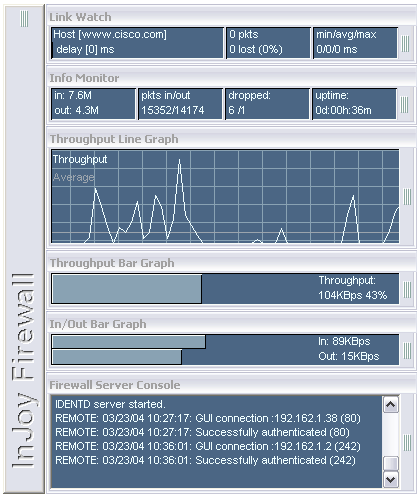
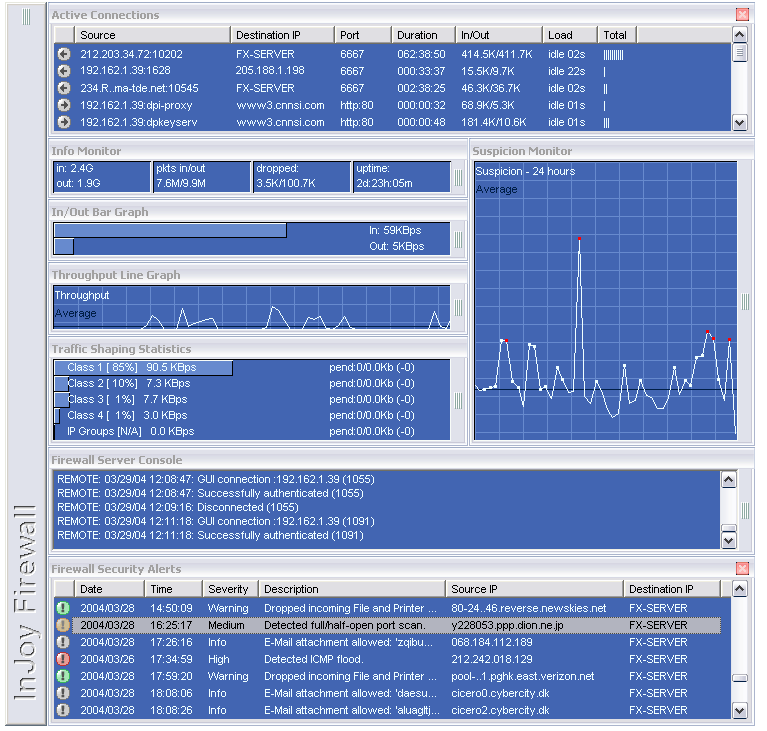
Measure
Through a series of sophisticated tools and GUI monitors, the InJoy Firewall™ provides new visibility into previously unknown activity taking place on the Internet servers:- The Security Alert Monitor provides color-coded real-time insight into almost any Internet
activity taking place on your Internet server. The level of information shown is fully
customizable and even your own firewall rules can log additional information to the security alert log.
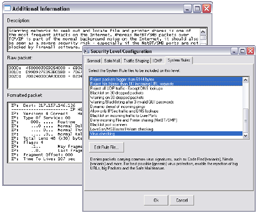
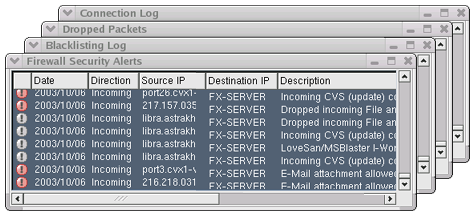
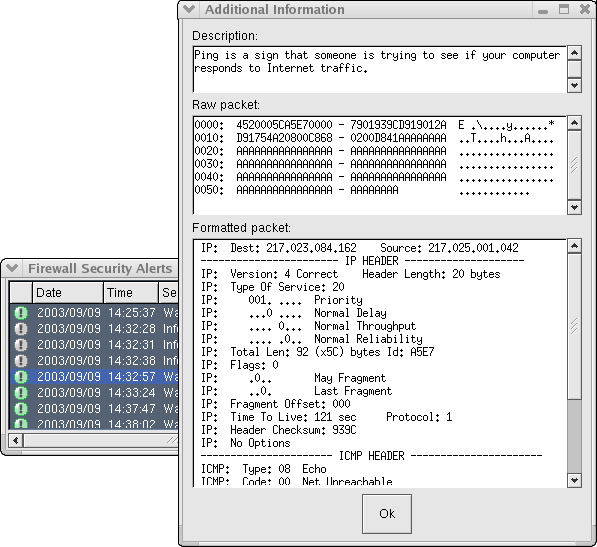
Note: The Firewall Security log records are expandable and as they are clicked, you will see a detailed description of the event, as well as a formatted and hex IP packet dump. - Other pre-configured Log Monitors measure the success rate of your security policy. Use the dropped packet log to see why individual packets are rejected; use the rejected TCP connection log to keep track of security policy violations; use the accepted TCP connection log as an access audit log. Also logged are hosts that are rejected by the dynamic blacklisting feature
- The HTTP Request Log measures the use of the http protocol and
allows the network administrator to keep track of both incoming and outgoing web requests.
Letting employees know that the corporate policy is to log all web surfing, is often all it takes to completely prevent an otherwise sensitive problem. - IP packet tracing directly from the desktop folder provides the network administrator packet-level insight into the traffic stream being processed by the Firewall. Through a drop-in firewall rule and an easy-to-use trace tool (ipformat), this feature quickly becomes indispensable.
- The firewall rule monitor allows you to keep track of your regular firewall rules and also the dynamically created rules — including their match count and description.
- Other plugin-specific monitors allow you to measure the operation of the individual plugins. For example, keep track of the IPSec tunnels and their users, active DHCP Server leases, NAT users and their individual data-transfer statistics, etc.
One of the best ways to keep the network safe is to regularly monitor it on a proactive basis, looking for potential problems before they can turn into big problems resulting in unexpected downtime. Nothing enables you to better do this, than the highly customizable and easy-to-use multi-platform Graphical User Interface (GUI) of the InJoy Firewall™.
Configure
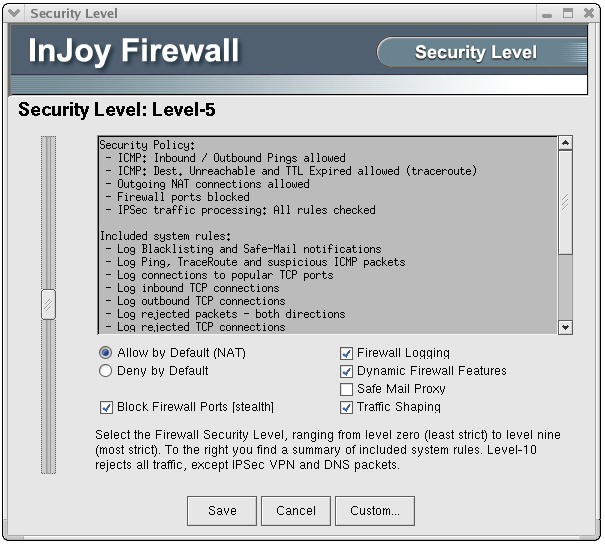
The InJoy Firewall™ GUI Administration includes powerful, local/remote/cross-platform configuration of every major Firewall component:- The Security Level dialog offers easy access to the well-conceived set of default policy templates. These fully customizable policy templates control which InJoy system rule files are to be included in the basic security policy, which traffic shaping classes exist, whether firewall ports are to be stealthed, and whether e-mail attachments will be screened.
- The Rule Workshop enables you to easily create Firewall rules of any type, including whitelist rules, blacklist rules, logging rules, deny rules, allow rules, NAT rules, traffic shaping rules, alert rules, account rules and more... The rule workshop can be operated both in simple and advanced mode.
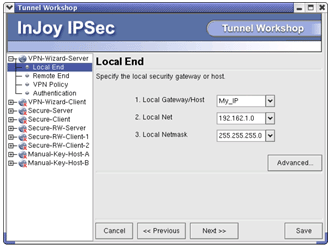
- The VPN Wizard provides a simplified, template-based interface to IPSec, allowing anyone to easily set up a VPN.
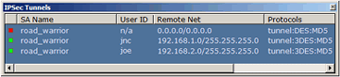
- The IPSec Tunnel Workshop provides you full access to the IPSec security associations. Ready-to-deploy samples are included.
- The IPSec User Administration provides easy configuration of VPN users in the simple built-in user database.
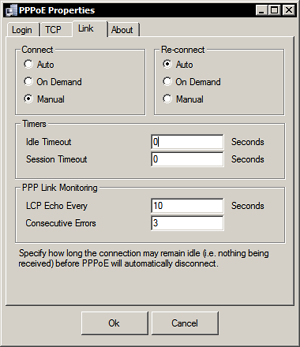
- The PPoE Broadband Access is set up in the PPPoE configuration dialogs, which provides easy configuration of multiple ISP profiles, demand connections and link monitoring.
- The DHCP Server Dialog provides extremely simple configuration of a simple DHCP Server profile and associated IP pools.
Though many users will opt to configure the InJoy Firewall™ and its components using the Firewall GUI, you can edit the InJoy Firewall's configuration files using any plain-text editor, such as Notepad or a programmer's editor.
Manage
The public tolerance for badly designed software is wearing thin. bww bitwise works GmbH witnesses the annoyance everyday, as bewildered users — tired of wrestling with illogical devices — request our services. With the easy-to-use enterprise-grade management features of the InJoy Firewall™, administrators can benefit from years of accumulated field-experience:- Local or Remote management. The InJoy Firewall™ separates the firewall server process from the desktop management GUI application. This allows you to manage your firewall from anywhere; either locally through shared memory or remotely, over a compressed, AES encrypted and audited TCP/IP connection.
- Manage from any supported operating system. The GUI is platform interoperable, allowing you to control e.g. a Linux based InJoy Firewall™ Server from Windows. The remote GUI license included in the Pro and Enterprise packages allows unlimited multi-platform use — with no extra licensing.
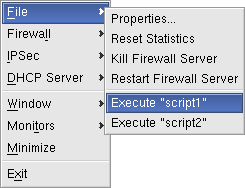
- Simple commands to stop/restart the remote firewall server, reset statistics, and reload configurations ease the overall management.
- Remote script execution allows the firewall administrator to start two pre-named scripts remotely, for example to save a snap-shot of the firewall logs, perform automated software installation of a new client-package, download security updates, or to perform any other administrative event.
- Quick blacklisting allows you to immediately respond to whatever suspicious behavior you encounter. For example, if a host won't stop pinging you or you think you are on to a potential hacker, simply use the Quick Blacklist feature to block that specific IP address (or a whole range of IP addresses).
Superior Firewall Protection
The Firewall Security Plugin is an integrated component of the InJoy Firewall, providing you an impressive range of features to monitor network activity, control access, and automatically block any type of potentially dangerous traffic.10+ predefined Security Levels — all fully customizable and with clear summary descriptions, allow you to easily configure the protection you need.
What is protected?
The InJoy Firewall™ is typically installed to the Internet-connected network card, protecting the private network(s) and also the computer it is installed on. If you have several insecure network cards, multiple (separate) instances of InJoy Firewall™ can be installed.
Executive Overview
Below are just a few of the reasons why you should download and use the InJoy Firewall™. Once you have enjoyed intuitive, manageable and complete firewall protection, we are confident you will not want to do without it.- Complete "Deep Packet Inspection" Security
Provides unprecedented broad-scoped security and enables the network administrator to effortlessly eliminate (D)DoS attacks, trojans, worms, SYN floods, ICMP floods, port-scanning, e-borne viruses, executable e-mail attachments and many other threats. - Protection "Out of the box"
Experience shows that many firewall users never make it beyond the default configuration, which is why the InJoy Firewall™ — by default — ships with comprehensive firewall protection and logging. - Unified end-point security
Multi-platform support ensures a universal defense and allows the same level of end-point security to be deployed throughout the organization. - Open and customizable
The default 'Security Levels' and 'System Rules' are defined in a hierarchy of text-files, allowing you to easily construct organization-optimized Security Levels or modify existing levels. The resulting Security Levels are easily distributed to clients or deployed on remote computers. - Powerful visualization and reporting
A wealth of pre-configured easy-to-understand monitoring features provide administrators with new visibility into previously unknown activity taking place on the Internet servers. - Web filtering and URL monitoring
Control and monitor employees' use of the web and eliminate lost productivity. With built-in HTTP address monitoring and filtering it is easy to enforce the company's acceptable use policy. - Handy security enforcement tools
Manual blacklisting allows you to instantly block a suspicious host from the GUI, without cluttering your overall security policy. Built-in IP packet tracing capability from the desktop folder provides you an always convenient method of analyzing new threats.
10 Powerful Defense Measures
The InJoy Firewall™ provides a multi-leveled and multi-faceted approach to securing Internet connections. By submitting all Internet traffic to multiple layers and by checking special traffic with a number of specialized features, the overall threat detection becomes more effective. Here's how:- Multi-layered enterprise-class security combines proven technologies, including stateful inspection and static signatures, with dynamic next-generation intrusion protection, behavioral rules technology, dynamic blacklisting, virus checking and much more...
- A fine-mesh detection net
The default security levels provide static signatures and dynamic rules to pick up on any first signs of hacking/intrusion/abnormality, such as:- Policy violations
- Unexpected or dangerous use of network protocols
- Any known attacks and exploits
- Any type of port-scanning
- Failed network access
- Login failure with common services
- Failed 'Remote GUI' login attempts
- Floods - DOS attacks
- Excessive amounts of dropped packets
- Malicious HTTP URL requests
- Uncommonly big packets
- More...
- Blacklisting
Dynamic (and also manual) blacklisting rules completely block access for a remote host after confirmed security violations — either permanently or for a defined period. - The observation list
The observation list maintains a list of dynamically created rules, which uses an offense hit-count to holistically and reliably detect subtle threats — without false positives. For example, if your Internet server is pinged, a dynamic observation rule might be created to ensure that your server isn't ping-flooded by the remote user. - Dynamic rules
Dynamic rules provide a new level of protection, as they allow the security policy to intelligently adapt. Static rules can dynamically change behaviour when matched or trigger the creation of completely new rules. A new rule can continue to monitor questionable activity for a particular user, now bearing with it a small history.
Dynamic rules also offer unprecedented support for constructing dynamic access policies. For example, you could use a dynamic rule to allow access to a particular network service, only after a special other network service is first used. The possibilities are endless. - Protocol validation
Inspects whether traffic adheres to the expected use of the protocol, minimizing the risk of buffer overflows in standard network services, such as HTTP and SMTP. - Application-level vulnerability protection
Prevents damaging and long URL requests from reaching your web server, thus minimizing the risk of application vulnerabilities being exploited. - Server based E-mail protection
The SMTP e-mail proxy prevents all e-mail borne executable viruses, trojans and worms from reaching the internal computers. You can either rename the executables, deny them or simply log them. The SMTP proxy also provides relay control and optionally blocks gigantic e-mails. - Packet integrity checking
All packets traversing the InJoy Firewall™ have their integrity checked to guard the operating system from malformed packet exploits and fragmentation vulnerabilities. All dropped packet are logged. - Network Address Translation
NAT is a standard feature for Internet sharing that also increases security by hiding internal IP addresses. With NAT, all outbound traffic appear to originate from the firewall's external network IP address.
Imagine a static rule that detects an incorrect FTP login. A single failed login is hardly enough reason to blacklist the remote user, however it does give reason to raise awareness.
To further monitor the activity of the offending user, the static rule can create a new dynamic rule and check if the remote user might fail to login with FTP yet again. If a second FTP login failure is observed from the same user, the first dynamic rule can create yet another dynamic rule to blacklist the remote user for a period of time.
Predefined Logging
The InJoy Firewall™ is pre-configured to maintain a variety of detailed logs. Logging provides a record of (questionable) activity over time and allows the network administrator to detect configuration problems, construct new firewall rules, carry out investigations, and perform other useful security tasks. All pre-configured log files can be monitored in real time from the Firewall GUI.- Security Alerts
This is the most important log for the Firewall administrator. It includes a description of the security alerts and their severity.
When extra information is available, the log record can be clicked to present a full description, a formatted trace of the offending packet and also a hex dump. - Rejected Connections
Any TCP connection not accepted by the InJoy Firewall™ is logged to this file, with time stamp, direction, IP numbers, and port numbers. - Connection Log
Any incoming and outgoing TCP connection is logged to this file. The log includes a record for both TCP connection initiation and termination. - Dropped Packets
To increase the product transparency, any packet dropped by the InJoy Firewall is logged to this file. Each log file entry lists the cause of the rejection and even the name of the firewall rule, in case the packet was rejected by policy. Dropped packets can be clicked to show the actual packet. - Blacklisting Log
Monitors the list of hosts which have been blacklisted (blocked) after violating the Firewall rules. The cause of the blacklisting is also logged. - HTTP Request Log
Monitors the HTTP requests which have passed through the InJoy Firewall™.
Logging can be defined for any rule, providing the administrator complete control over the logging files created, their location, their maximum size and their content.
Rule Lists
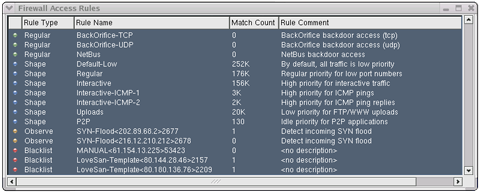
Firewall Access Control Lists (ACLs) make a powerful tool for the firewall administrator to control in a practical way how the firewall treats any IP traffic. The InJoy Firewall™ supports six groups of rules - evaluated in the following order:- Whitelist rules
Packets matching Allow rules on this list are unconditionally passed through to your Firewall PC, while packets matching NAT rules are passed on to NAT processing for further inspection. Whitelisted traffic bypass all other rule lists. - Blacklist rules
Packets matching rules on this list are unconditionally rejected. - Observation List rules
Rules on this list are created automatically by the InJoy Firewall™ System rules, in order to keep track of suspicious behavior. - User rules
On this rule list, the network administrator defines the granular access that makes up the organization-specific security policy. - Traffic Shaping rules
Rules on this list are used to prioritize traffic and impose bandwidth constraints. - InJoy Firewall™ System rules
These rules are shipped with the InJoy Firewall™ and serve as the foundation for the security levels.
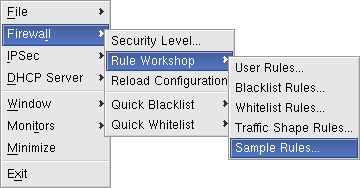
Rule Monitoring
A special firewall monitor called Firewall Access Rules displays the list of rules that are active for the currently running Firewall Server.Rules from every rule list appear in the Access Rules monitor, including system rules, blacklist rules, and so forth. The icon to the left indicates the type of rule. For each rule in the monitor, you will see a name, a description, and the number of packets that have matched the rule.
The Firewall Access Rules monitor also shows the dynamically created rules, enhancing your understanding of the firewall engine activity.
Manage Bandwidth with Traffic Shaping
The traffic of one or more full-speed download sessions take its toll on the overall network performance. The results are:- Slow web page access and downloads for your customers.
- Network congestion among internal work-stations.
- Lack of responsiveness with interactive services, such as VoIP.
- Random Bandwidth depending on the activities of just a few people.
Introduction
The InJoy Firewall's Traffic Shaping feature offers a solution to the problems mentioned above, by providing easy-to-use bandwidth management and traffic prioritizing capabilities. Additionally, in version 4.0 of InJoy Firewall, the code has been hardened to get even more precise and fair distribution of available bandwidth between the Internet sessions.- Central control
Traffic shaping is performed centrally on the gateway computer and no special software is required on the LAN work-stations. - Rule driven
With simple firewall rules identifying the traffic to shape, packets can be assigned to a special priority queue or bandwidth can be managed by the rule itself. The rule driven traffic shaping enables you to individually shape any type of traffic and you can also combine traffic shaping with other powerful rule based features, such as time-dependency. - Measurable
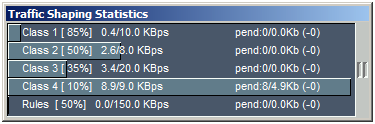
Through rule-matching counts, the InJoy Firewall™ access rules monitor provides you with real-time insight into the distribution of packets among individual shaping rules. For a more visual presentation, the Traffic Shaping Statistics monitor allows you to follow the packet distribution in real-time. - Pre-configured Samples Popular ready-to-deploy traffic shaping examples are included and if you just enable traffic shaping in the InJoy Firewall™, it's preconfigured to prioritize your traffic.
Traffic Shaping Features
- Priority Packet Queues
By placing different types of traffic in different queues and then assigning these queues
different priorities, you can control the order in which packets are de-queued and sent.
The InJoy Firewall™ ships with 4 priority queues and a number of traffic shaping rules that make use of these queues.
True idle queues - The InJoy Firewall™ uniquely makes use of OS thread scheduling to prioritize traffic, thereby allowing certain low-priority activities to only take place when the CPU is truly idle. This powerful feature completely prevents important traffic from being affected by less-important, yet high-speed traffic - such as Internet based backup, P2P or game server traffic. - Bandwidth capacity per rule
Rule based traffic shaping allows a single firewall rule to limit the bandwidth capacity of all matching traffic. For example, through a single firewall rule, you can limit all outgoing ftp traffic to 10K per second or limit the traffic of an individual user. The possibilities are endless. - Group based Traffic shaping
Each host matching a specific rule is provided a 'virtual' pipe of fixed bandwidth capacity. With this method of bandwidth management, it is impossible for one user to affect another in any way. Use this type of bandwidth allocation, to e.g. distribute a maximum of 1Mbps evenly between internal users. - Small TCP Packet Promotion
As you download big files and web-pages, your PC has to constantly send small ACK packets to acknowledge the received data. On busy connections, ACK packets are held back by less important traffic and this round-trip latency decreases the download speed. The InJoy Firewall™ includes technology to promote the ACK packets, thus generally increasing your download speed. - Overall Bandwidth Limitation
Limiting the overall bandwidth in either the incoming or outgoing direction allows you to e.g. accommodate special ISP limitations (e.g. capacity-based billing) or prevent ADSL router queues from running full. The resolution is one kilobyte per second.
Default Priority Queues
The InJoy firewall™ ships with traffic shaping turned off, however the following traffic priority classes are defined - waiting to be enabled:- Priority Class 1 - Running at high priority - 85%
- Priority Class 2 - Running at normal priority - 50%
- Priority Class 3 - Running at low priority - 35%
- Priority Class 4 - Running at idle priority - 10%
Default Traffic Shaping rules
Firewall rules can assign certain types of traffic to certain types of priority classes. The InJoy firewall™ does it like this - per default:- All traffic is placed in the low priority queue (3) by default.
- Traffic on ports 1-1024 are placed in the normal priority class (2).
- Interactive traffic of protocols such as: telnet, ssh, www, icq, dns, ftp port 21, irc and ICMP, are placed in the high priority queue (1).
- Outgoing www and ftp data connections (i.e. uploads from your Internet server) are specifically placed in the low-priority queue (3).
- Peer-to-Peer traffic in placed in the idle priority class (4).
IPSec VPN Client / Server Support
Transparent, standards-based cross-platform unified IPSec technology, extends the InJoy Firewall™ with capability of building VPN's and secure channels — allowing corporations to deploy it either as a VPN Gateway or as a secure VPN Client.With the simple IPSec VPN Wizard, even beginners can now set up a company-wide VPN.
What is an IPSec VPN and why do I need it?
An IPSec VPN uses modern encryption and authentication technologies to keep the data that it carries private — hidden from public view and completely protected against unauthorized access or theft.
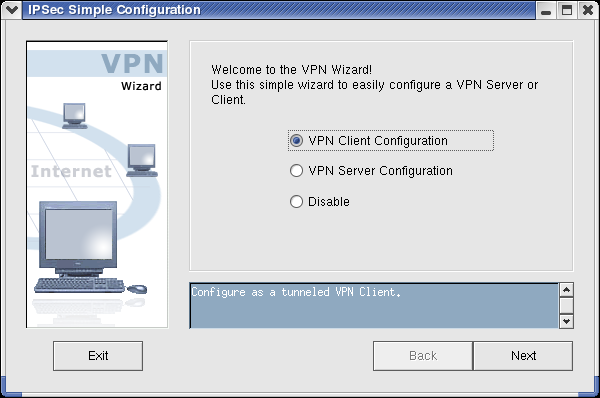
IPSec VPN benefits
Technology from one of the world's leading IPSec Toolkit providers extends the InJoy Firewall™ with unique IPSec benefits:- Easy to use and designed to boost your productivity. Includes step-by-step GUI based configuration, a built-in user database, deployment examples, and a wealth of convenience features.
- Seamlessly installed and optional, the InJoy IPSec™ is implemented as a modular plugin. Simply opt not to load it and it won't take up resources or add complexity.
- IPSec Client and Gateway support in one application eases the configuration on both ends.
- Firewall Integration to specifically filter, log and otherwise control IPSec traffic. To further ease the setup of a popular configuration, the InJoy Firewall™ even includes a pre-configured security level that blocks all non-IPSec traffic.
- Cross-platform unified operation ensures fast deployment throughout the organization.
- Standards-based and third party interoperable. Tested with public test engines and an extensive range of market-leading VPN solutions.
IPSec VPN Features
InJoy IPSec™ includes all the latest features and a comprehensive palette of business-ready protocols:- High-grade encryption standards, including U.S. government adopted AES (Advanced Encryption Standard), 3DES, Blowfish, DES and NULL encryption.
- Powerful Authentication through Pre-Shared Keys (PSK), Extended Authentication (X-Auth), RSA signatures, x.509 Digital Certificates and Group Authentication. Password prompting supported to avoid storing of passwords on the harddisk.
- External Authentication provides possibility to store password and other sensitive data in an external storage, like MySQL.
- NAT Traversal facilitates easy IPSec deployment over NAT connections.
- IP Compression delivers maximum bandwidth through LZS or DEFLATE compression.
- Dynamic IP (Road Warrior) Support allows you to accept IPSec connections from hosts whose IP addresses you do not know in advance.
- Split tunneling allows a host to maintain tunneled VPN communications with other hosts in the VPN while at the same time communicating with public Internet hosts directly, outside the tunnel. This reduces both processing and traffic overhead on the private network.
- Virtual IP allows the VPN administrator to assign an internal (virtual) IP address to any IPSec client to unify the internal IP address range.
- Fail-over and Fall-back allows InJoy IPSec to "fail-over" to another VPN Server when the primary one fails, and then "fall-back" to the primary VPN Server when it starts working again. Additionally, Path MTU Discovery technology support provides smooth operation in aggressive IP networks with MTU (Maximum Transmissions Unit) sizes lower than usual.
- Wide protocol support, including manual and automatic key exchange, tunnel and transport mode, main-mode and aggressive mode.
Deployment and user friendly
Interoperability issues inspired the creation of the 100% standards-based multi-platform InJoy Firewall™ product, with which complicated VPN configuration, IPSec interoperability issues, and multi-platform concerns are a thing of the past.- Step-by-step GUI Configuration Wizard
If your IPSec VPN requirements include tunneling, encryption, authentication, a simple user-database, a single network at each location, and a number of remote VPN Clients, then use the new VPN Wizard to simplify configuring InJoy IPSec at each of the endpoints.
The VPN Wizard makes use of preconfigured templates for both the VPN Server and Client. The Server is configured to accept connections from both fixed and dynamic IP addresses, even through a NAT Gateway. It authenticates the VPN Clients through Preshared Keys (a password) and through the user-account based Extended Authentication protocol.
You decide what encryption standard to use, specify what network is behind each IPSec endpoint, maintain the IPSec VPN user database and assign a Virtual IP address to the remote VPN Clients directly from the VPN Wizard.
The VPN Wizard configuration can be carried out locally or remotely, allowing the network administrator to maintain a complete VPN network from a central location. - Tunnel Workshop
For complicated VPN configurations, InJoy Firewall™ supports both local and remote configuration of the Security Association database. Live on-screen help and ready-to-use samples provide the ease of use required by busy professionals. - Rapid deployment
Comprehensive documentation, a VPN case study and a wealth of deployment examples enable rapid deployment. External utility programs, on-the-fly configuration updates and the possibility of plain text configuration enables easy administration and maintenance. - Extra Productivity
The Maximum Segment Size (MSS) auto adjust feature prevents the administrative nightmare of IPSec introduced MTU problems. Perfect integration with the Firewall enables you to define security policies that affect IPSec users only. - Monitoring
Once IPSec is configured, you can make use of the IPSec monitoring capabilities to locally or remotely monitor IPSec tunnels, internal users that have made use of the tunnels and IPSec security logs.
It requires you to:
- License proper products - often from multiple vendors.
- Define an even VPN configuration, among un-even products.
- Ensure the products yield the latent capacity for your company's future expansion.
- Learn multiple products.
Internet Gateway Capability
With no reconfiguration of network applications, the Network Address Translation (NAT) feature provides optimized and transparent Internet access for all computers on your private network.Out of the box Internet Sharing for up to 1000 computers on your private network(s) — with top performance.
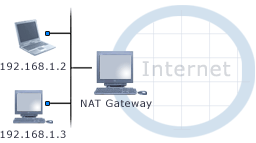
Complete Internet Gateway Support
The InJoy Firewall™ is pre-configured to deliver secure NAT routing for your internal network. Simply install the InJoy Firewall™ on the computer with the Internet connection and configure the internal LAN clients to use the Firewall PC as their Default Gateway.- Internet Sharing
By default, the InJoy Firewall™ is configured (but not limited) to provide NAT for the well-known reserved ranges of internal IP addresses:- 10.0.0.0 through 10.255.255.255
- 172.16.0.0 through 172.31.255.255
- 192.168.0.0 through 192.168.255.255
- Seamlessly integrated
InJoy NAT operates in full accordance with the chosen Firewall security policy and it is tested for compatibility with IPSec NAT-Traversal, PPPoE and PPTP.
Comprehensive real-time statistics for the internal LAN clients is available through the NAT monitor of the InJoy firewall™ GUI. - Simple DHCP Server (plugin)
Configuring a full-blown DHCP (Dynamic Host Configuration Protocol) Server can be complicated and may require more time, then the benefit of having it might justify. To simplify the task, the InJoy Firewall™ includes an extremely simple DHCP Server Plugin, supporting assignment of all the basic DHCP parameters:- IP address and subnet mask
- IP addresses of up to 3 DNS/WINS servers
- The default gateway
With DHCP enabled... it suffices to enable the "Obtain an IP address automatically" in the TCP/IP configuration on the private network. The DHCP Server then takes over the responsibility of assigning the TCP/IP parameters, significantly lowering the task of network maintenance.
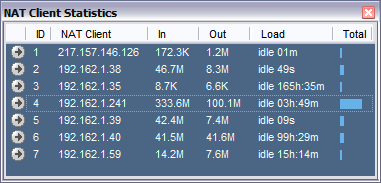
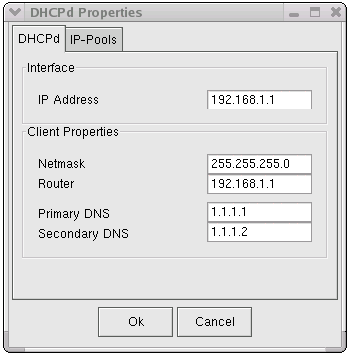
Intermediate Convenience Features
- MSS Auto Adjust
The MSS (Maximum Segment Size) Auto Adjust feature automatically tweaks the MSS value in the TCP connection setup, to force hosts to exchange slightly smaller TCP data packets.
Smaller data packets prevent the extremely common MTU problems, which were mainly introduced by complex packet-enlarging features, such as IPSec, NAT, PPPoE and PPTP.
The typical MTU problems are web pages that won't fully load, large e-mail attachments that won't transfer properly and file-transfers that stalls after the first few packets. All these problems are typically solved by this extremely powerful convinience feature. - DNS Forwarding
The InJoy Firewall™ has built-in DNS Forwarding to further simplify the configuration of internal work-stations. Simply point the internal work-stations to the DNS servers 1.1.1.1 and 1.1.1.2. The InJoy Firewall then forwards DNS queries on to the public DNS server addresses configured in the InJoy Firewall™.
NAT vs. Proxy Technology
While several viable Internet sharing technologies exist, the NAT standard has during the past few years proved itself as the prevailing Internet gateway technology.The alternative to NAT, is a collection of application proxies. These proxies set up two TCP connections to relay traffic between the network service and the remote user. Proxies offer some benefits, such as user authentication options and application-level control, however due to their complexity, they tend to be both bug-filled, slow and hard to maintain.
Today's networking applications are designed to interact with NAT devices and while application proxies remain applicable for some Internet protocols, they are often seen phased out as the primary Internet sharing technology.
For the best of both worlds, the InJoy Firewall™ uses NAT as the core Internet sharing technology and also includes several proxies, such as the SafeMail and identd proxy server.
Broadband / PPPoE Client Support
The InJoy Firewall™ supports a wide range of external Internet connections, including, but not limited to xDSL, Cable, dedicated T1 circuits, Frame Relay and even satelite connections. The InJoy Firewall™ can also be used on internal networks to separate two network segments or to provide custom scecurity on special PCs.Multiple Access Technologies:
- Ethernet Based Connections
The InJoy Firewall™ supports Ethernet based connections of any type, with either static or DHCP served IP numbers. - PPP over Ethernet (PPPoE)
A growing number of Internet Service Providers (ISPs) are implementing PPPoE to replace the static IP addressing or DHCP systems that do not offer authentication, billing, or service differentiation.
With the seamlessly integrated InJoy PPPoE plugin, users enjoy automated link monitoring, demand connections, and scripting in order to maximize the use of dynamic IP addresses. - Point to Point Tunneling Protocol (PPTP)
Using the Point to Point Tunneling Protocol (PPTP), you can dial the Internet service providers that rely on this protocol, or use PPTP tunneling to connect to the corporate network via the Internet. PPTP support is the InJoy Firewall™ is primarily included to provide connectivity to the still limited number of ISPs that rely on this protocol. The IPSec protocol is recommended over PPTP for Virtual Private Networks.
Firewall Technology Brief
The InJoy Firewall™ framework is built around InJoy's own hardened low-level device driver technology on each supported platform. This allows the InJoy Firewall™ to offer protection without exposing the Operating System to malicious traffic.Similar to hardware firewalls, the InJoy Firewall™ framework is designed to deliver robust stand-alone operation, ensuring optimal performance, minimum heredity of third-party issues and perfect internal integration.
The InJoy Firewall™ does not rely on the host Operating System for any of the major features, including IPSec VPN Support, Firewall Security, DHCP Server support, PPPoE or PPTP. These features are implemented from the ground up using InJoy's own hardened codebase, in order to be as secure and flexible as possible for mission critical environments.
Separate GUI and Firewall Server
For maximum flexibility and remote administration capability, the InJoy Firewall™ solution separates the Firewall Server process from the desktop management application. The operating Firewall can be thought of as two components:- Firewall Server
Text mode application, which provides the actual Firewall functionality, loads feature plugins and acts as a server for the Firewall GUI. - Firewall GUI
Provides local and remote enterprise-grade management capability for remote Firewall Servers.
The GUI connection uses shared memory for local operation and a compressed, AES encrypted TCP/IP connection for remote connections. Because the GUI is optional, it can be started and stopped on demand as the Firewall Server runs.
OS Platform Independence
The InJoy Firewall™ relies on commonly available operating system technologies to deliver native performance and a common user interface on all supported OS platforms. Tunking layers are avoided for optimal performance and native user-interface controls are preferred over a less powerful Java implementation or a slow web interface. Read more>>One Firewall per Insecure Network Interface
The InJoy Firewall™ Server process is designed to protect individual network connections, thereby providing a single location for packet analysis and packet filtering. Multiple, autonomous instances of the InJoy Firewall™ can easily be installed in situations where multiple insecure network interfaces need protection.Fault Tolerant
The InJoy Firewall™ gives you the option to disable all traffic automatically during installation in case the Firewall Server process becomes inactive for any reason. This feature provides an extra layer of security for your internal network when unexpected hardware or software difficulties arise.Plain text configuration also possible
Many users will opt to configure the InJoy Firewall™ and its components using the Firewall GUI whenever possible. But administrators also have the option to manage the InJoy Firewall using plain-text onfiguration files resulting in the following advantages:- Ease of distribution.
- Ease of preservation.
- Increased efficiency.